A groundbreaking security research study has uncovered a critical vulnerability that could fundamentally undermine the security and reliability of artificial intelligence systems. The discovery reveals how a hardware-level attack called Rowhammer can be weaponized against GPU memory to completely destroy AI model performance, raising serious concerns about the security of machine learning infrastructure in shared computing environments.
Understanding the Rowhammer Attack
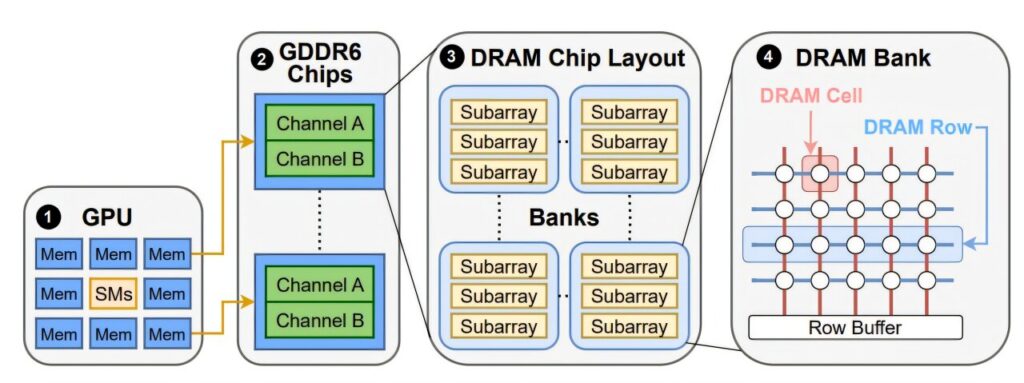
Rowhammer represents a sophisticated class of hardware attack that exploits the physical properties of modern memory systems. The attack works by repeatedly accessing specific memory locations at high speed, creating electrical interference that can cause nearby memory cells to spontaneously flip their stored bits from 0 to 1 or vice versa.
This phenomenon occurs due to the increasingly dense packing of memory cells in modern hardware. As manufacturers squeeze more storage capacity into smaller spaces, the electrical isolation between adjacent memory cells becomes weaker, making them susceptible to interference from neighboring operations.
While Rowhammer attacks have been well-documented on traditional CPU memory systems, researchers have now proven that the same vulnerability exists in Graphics Processing Unit (GPU) memory, specifically in GDDR (Graphics Double Data Rate) memory designed for high-performance computing applications.
The Devastating Impact on AI Models
The research team’s findings reveal just how catastrophic this vulnerability can be for artificial intelligence systems. In their controlled experiments, flipping just a single bit in an AI model’s weight parameters was sufficient to completely destroy the model’s performance.
The results are staggering: accuracy dropped from 80% to a mere 0.1% with just one corrupted bit. This demonstrates the extreme sensitivity of machine learning models to even minor data corruption, highlighting a fundamental weakness in how AI systems store and process information.
This vulnerability is particularly concerning because AI models contain millions or billions of parameters stored as numerical weights. These weights represent the “learned knowledge” of the model, accumulated through extensive training processes. When even one of these weights is corrupted, it can cascade through the entire system, producing completely unreliable results.
GPUHammer: Adapting the Attack for Modern AI Hardware
The research team, led by security experts, developed a proof-of-concept attack they dubbed “GPUHammer” specifically targeting NVIDIA RTX A6000 graphics cards—hardware commonly used in professional AI development and deployment.
Adapting Rowhammer for GPU memory presented unique technical challenges. GPU memory systems operate differently from traditional CPU memory, requiring researchers to develop new hammering patterns and timing strategies to successfully trigger bit flips in GDDR memory.
Technical Innovation Required: The team had to reverse-engineer the specific memory access patterns that would create sufficient electrical interference in GPU memory systems. This involved understanding the unique architecture of GDDR memory and how it responds to repeated access patterns.
Successful Exploitation: Despite these challenges, the researchers successfully demonstrated that GPUHammer could reliably corrupt GPU memory, proving that the theoretical vulnerability translates into a practical attack vector.
Cloud Computing: The Perfect Storm
The GPUHammer vulnerability becomes particularly dangerous in cloud computing environments where multiple users share the same physical GPU hardware. This shared infrastructure model, while cost-effective and efficient, creates an ideal attack scenario.
Multi-Tenant Risk: In cloud environments, multiple virtual machines or containers may share access to the same GPU. An attacker with access to one virtual environment could potentially use GPUHammer to corrupt the memory used by other users’ AI workloads running on the same hardware.
Stealth Attacks: The attack could be particularly insidious because the corruption occurs at the hardware level, potentially bypassing traditional software-based security monitoring systems. A malicious user could sabotage competitors’ AI models without leaving obvious traces in system logs.
Economic Implications: For businesses relying on cloud-based AI services, this vulnerability could mean that their expensive model training or inference workloads could be silently corrupted by other users sharing the same hardware infrastructure.
NVIDIA’s Response and the ECC Dilemma
NVIDIA, the leading manufacturer of AI-focused GPUs, has acknowledged the vulnerability and recommended enabling Error Correction Code (ECC) as a mitigation strategy. ECC is a hardware feature that can detect and correct certain types of memory errors, including those caused by bit flips.
However, this solution comes with significant trade-offs:
Performance Impact: Enabling ECC memory protection slows down machine learning tasks by up to 10%, representing a substantial performance penalty for AI workloads that are already computationally intensive.
Economic Cost: The 10% performance reduction translates directly into increased computing costs, longer training times, and reduced throughput for AI applications—costs that many organizations may find prohibitive.
Limited Protection: Even with ECC enabled, researchers warn that more sophisticated attack methods could potentially bypass these protections, suggesting that ECC may provide only temporary security.
The Broader Implications for AI Security
The GPUHammer discovery highlights fundamental security challenges in the AI industry that extend beyond this specific vulnerability:
Hardware-Software Security Gap: Traditional cybersecurity approaches focus primarily on software vulnerabilities, but GPUHammer demonstrates that hardware-level attacks can be just as devastating for AI systems.
Infrastructure Trust: The vulnerability raises questions about the security of shared computing infrastructure, particularly in cloud environments where users must trust that their workloads are isolated from potential attackers.
AI Model Fragility: The extreme sensitivity of AI models to single-bit corruption reveals an inherent fragility in these systems that makes them particularly vulnerable to both accidental errors and malicious attacks.
Industry Response and Mitigation Strategies
The discovery of GPUHammer has prompted discussions across the AI and cybersecurity communities about potential mitigation strategies:
Hardware Design Changes: GPU manufacturers may need to redesign memory systems to be more resistant to Rowhammer-style attacks, potentially involving changes to memory cell isolation or access pattern monitoring.
Software Defenses: AI frameworks could implement integrity checking systems that periodically verify model weights haven’t been corrupted, though this would add computational overhead.
Operational Procedures: Organizations running AI workloads may need to implement new security procedures, including more careful vetting of shared computing environments and regular model validation.
Future Research Directions
The GPUHammer discovery opens several important areas for future cybersecurity research:
Attack Vector Expansion: Researchers will likely investigate whether similar attacks can target other types of AI hardware, including specialized AI chips and tensor processing units.
Defense Development: Security researchers will work on developing more efficient methods for detecting and preventing hardware-level attacks on AI systems.
Model Resilience: AI researchers may explore techniques for making models more resistant to parameter corruption, potentially through redundancy or error-tolerant architectures.
Implications for AI Development
The vulnerability has significant implications for how AI systems are developed and deployed:
Security by Design: AI system architects may need to incorporate hardware security considerations into their designs from the beginning, rather than treating security as an afterthought.
Testing Protocols: AI development teams may need to implement new testing procedures that evaluate model robustness against parameter corruption, not just traditional performance metrics.
Deployment Considerations: Organizations deploying AI systems may need to reconsider their infrastructure choices, potentially favoring dedicated hardware over shared cloud resources for critical applications.
The Economic Impact
The GPUHammer vulnerability could have substantial economic implications for the AI industry:
Increased Costs: Organizations may face higher infrastructure costs as they choose dedicated hardware or accept the performance penalties of ECC memory protection.
Insurance and Liability: The vulnerability may drive changes in technology insurance and liability frameworks as organizations seek protection against hardware-level attacks.
Market Dynamics: Hardware vendors that develop more robust security features may gain competitive advantages, potentially reshaping the AI hardware market.
Regulatory and Compliance Considerations
As AI systems become more critical to business operations and public services, the GPUHammer vulnerability may influence regulatory approaches:
Security Standards: Industry standards for AI system security may need to expand to include hardware-level vulnerabilities and attack vectors.
Compliance Requirements: Regulated industries using AI may face new requirements for ensuring the integrity of their AI systems against hardware attacks.
Risk Assessment: Organizations may need to update their risk assessment frameworks to account for hardware-level threats to AI systems.
Looking Forward: The Evolution of AI Security
The discovery of GPUHammer represents a wake-up call for the AI industry about the importance of comprehensive security approaches that address both software and hardware vulnerabilities.
As AI systems become more powerful and ubiquitous, the stakes for security failures continue to rise. The ability to completely destroy an AI model’s functionality with a single bit flip demonstrates just how critical robust security measures will become.
The challenge moving forward will be balancing security requirements with the performance demands of AI applications. Solutions that provide strong security without significantly impacting performance will be essential for the continued growth and adoption of AI technology.
Conclusion: A New Era of AI Security Challenges
The GPUHammer attack represents more than just another security vulnerability—it signals the beginning of a new era where AI systems face sophisticated threats at the hardware level. As the AI industry continues to mature, security considerations must evolve to match the sophistication of both the technology and the potential attacks against it.
For organizations deploying AI systems, the discovery underscores the importance of comprehensive security strategies that address not just software vulnerabilities but also the fundamental hardware infrastructure on which these systems depend. As AI becomes increasingly critical to business operations and decision-making, ensuring the integrity and reliability of these systems becomes paramount.
The GPUHammer vulnerability serves as a crucial reminder that in the rapidly evolving landscape of artificial intelligence, security must be treated as a fundamental design consideration rather than an optional add-on. The future of AI security will require unprecedented collaboration between hardware manufacturers, software developers, and security researchers to address these emerging threats comprehensively.